These apps are more like a glorified data farm.
Among the various categories of apps that exist out there, some by their nature store more of your personal information as compared to others. One such niche is dating apps that have gained momentum over the past decade. However, there’s something shady that has been going on all the while in the background.
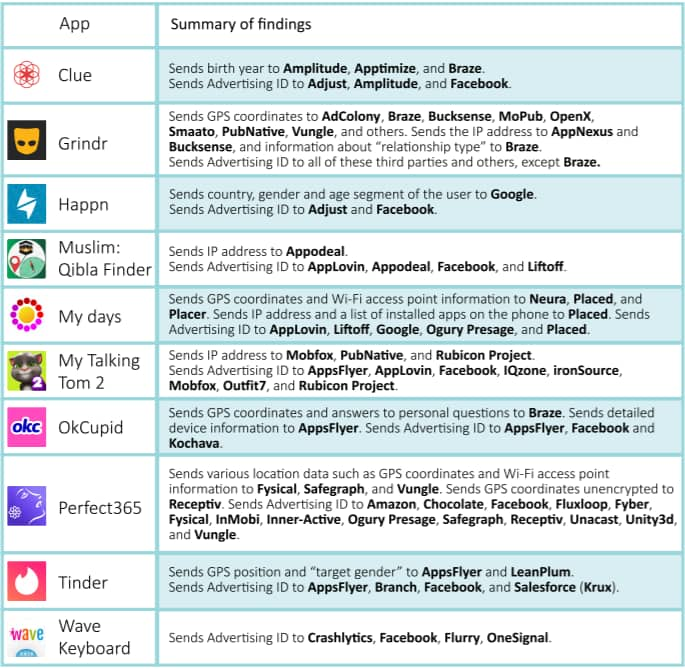
In a study [PDF] conducted by the Norwegian Consumer Council named Forbrukerrådet on 10 apps, it has been found out that several popular dating apps such as Tinder, OkCupid & Grindr along with certain popular menstrual help apps such as Clue and MyDays have been sharing the personal data of users with as much as 135 different third parties for advertising purposes.
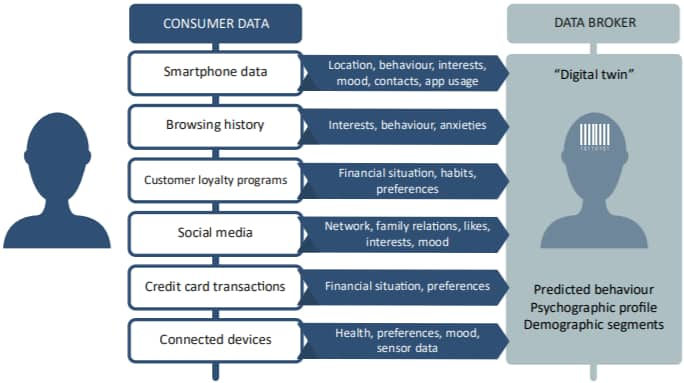
This data includes one’s location, age, gender, sexual orientation, drug use, religious & political views although varying from case to case depending on the information one has given to these specific apps.
Yet, we’ve seen this happening before and looks like no learned from it. Two years ago, Grindr was discovered sharing the HIV status’ of its users whereas Tinder was found giving away 100m accurate location data. The cause of alarm though lies in the fact that users at a fault too here.
You see, when one signs up to these apps, they are in some way agreeing to their privacy policies. Since both the policies of Tinder & OkCupid contain clauses that they may share your data with unspecified third parties, they may have a case of having your consent.
Moreover, it also states that they can share your data with any apps under their parent company: Match Group. So even if you haven’t ever used any other app than Tinder, 45+ other apps still have a right to access your data.
None of the apps provided the information necessary for the consumer to make an informed choice when launching the apps. Furthermore, we found a near-complete lack of in-app settings to regulate or prevent the sharing of personal data with third parties. This illustrates that consumers are often not given enough information to choose whether they accept being tracked and profiled, the study revealed.
Nonetheless, on the other hand, it is important to realize that these apps may be in violation of certain privacy laws such as the EU’s GDPR because of the secretive way in which they inform users of the handling of their data and how it is processed altogether. Hence, it is very important that they review their current policies and move forward in a legally compliant way.

Comments
Post a Comment