Currently, there are more than 800 million Windows 10 users across the globe while vast numbers of users are still using Windows 7. These stats may not come as surprise but they do make Windows users a lucrative target for cybercriminals.
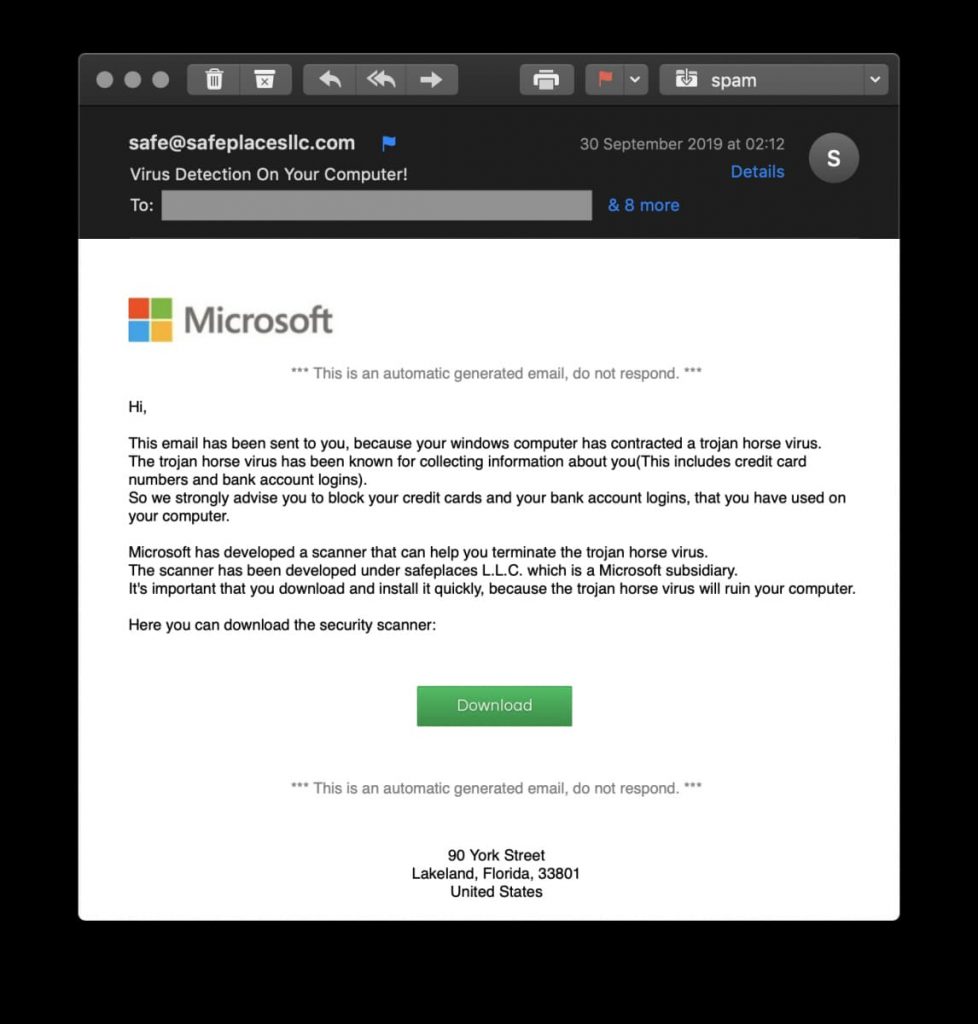
On October 3rd, 2019, a trojan horse was discovered which pretends to be a security scanner by Microsoft but in reality, it is everything evil but so. A cybersecurity researcher named Xavier Mertens first posted a screenshot of the email he received from the scammers prompting him to download the malware:
To start with, it can clearly be seen that the sender’s email address has not been spoofed to breathe in an air of authenticity. This blunder alone should be sufficient for most to realize that it is not a legitimate email but for the sake of exploration, we’ll continue.
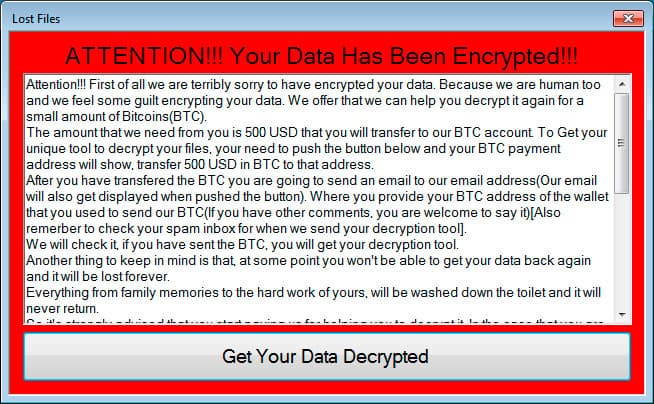
Upon downloading, we are presented with a WSS.zip archive file which contains the executable file of the fake scanner. Once one runs it, they are presented with aransomware warning a few moments later unfolding the entire scheme:
It’s not surprising that Bitcoin is their preferred currency but given some astonishing revelations surrounding its anonymity, Monero or Zcash certainly might have been a better choice.
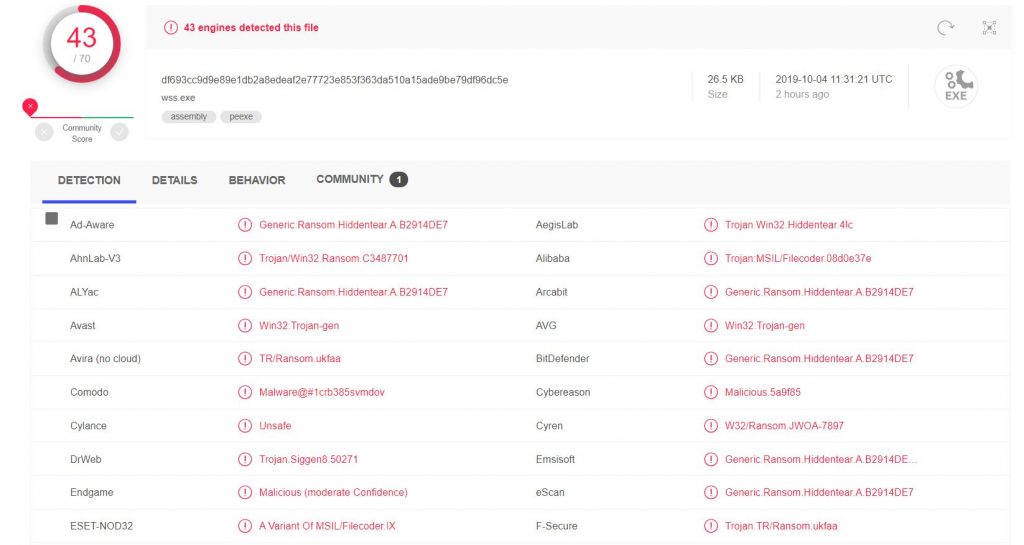
Upon inspecting the SHA256 of the archive with an online tool like VirusTotal, we are presented with the different categories and names under which it has been detected by various anti-virus software.
Regardless, after the tools has done its job, users would now find every file encrypted with the following types under the Users folder in C Drive bearing the”.Lost_Files_Encrypt” extension:
“.xxx .sdf .txt .doc .docx .xls .pdf .zip .rar .css .xlsx .ppt .pptx .odt .jpg .bmp .png .csv .sql .mdb .php.asp .aspx .html .xml .psd .bat .mp3 .mp4 .wav .wma.avi .mkv .mpeg .wmv .mov .jpeg .ogg.TXT .DOC .DOCX .XLS .PDF .ZIP .RAR .CSS .XLSX .PPT .PPTX .ODT .JPG .BMP.CSV .SQL .MDB .PHP .ASP .ASPX .HTML .XML .PSD .BAT .MP3 .MP4 .WAV .WMA .AVI .MKV .MPEG .WMV .MOV .OGG and .JPEG.”
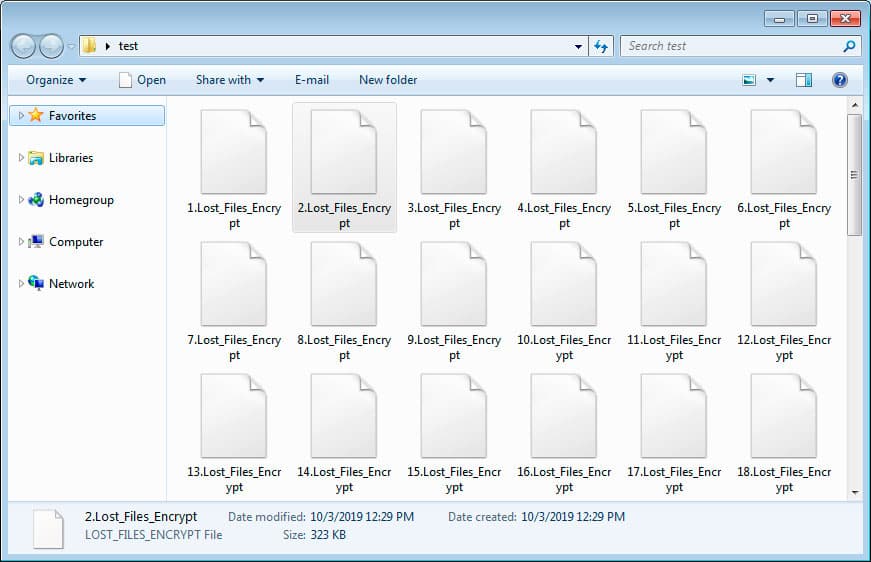
Image credit: Bleeping Computer
To conclude, this ransomware is no different from others. In fact, it is much easier to spot at first sight from the other ones out there but users getting compromised despite that says a lot about the lack of awareness surrounding cybersecurity. This is best summed up from a quote by Elliot from the famed Mr.Robot,

Comments
Post a Comment