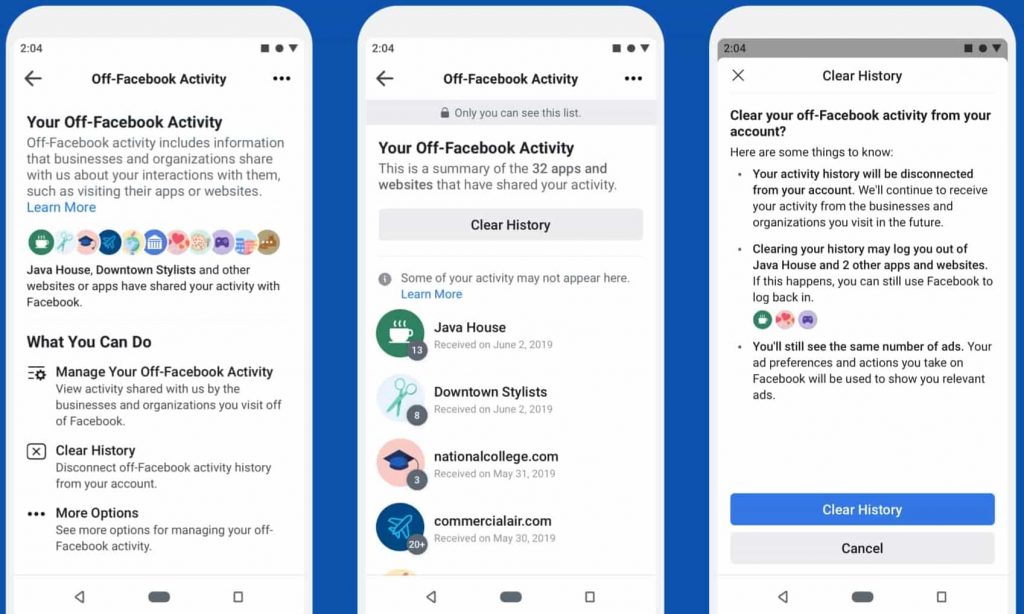
Off-Facebook Activity lets users see a summary of the apps and websites that send Facebook information about their activity.
Over the past decade when we saw Facebook shifting from just another social network, it greatly expanded its feature range. With this, tools such as “Facebook Login” and “Facebook Pixel” were launched.
In the case of the former, website owners can record your information when you use Facebook to log in onto their sites and then use this to display targeted ads. For the latter, it is a tool that allows website owners to integrate a piece of code which can be used to track site visitors and their actions. Later on, the data gained by tracking those users can be utilized for better ad targeting.
With this, in a bid to increase transparency, Facebook has launched yet another feature working with its privacy experts. Dubbed as “Off-Facebook Activity”, it comes as a fulfillment of the announcement CEO Mark Zuckerberg made last year along the lines of,
“Once we roll out this update, you’ll be able to see information about the apps and websites you’ve interacted with, and you’ll be able to clear this information from your account.”
What this means is that you can now view all the data that third-party app and websites have been sharing with Facebook and not only anonymize it but also turn off future data collection activity. For example, if I find Amazon collecting my “likes & shares” for some reason, I could restrict that if I wanted to with this new tool.
However, as evident from the screenshots above, a downside is that if you choose to disconnect the data-sharing capability with a specific website or app, you’ll also be instantaneously logged out from that respective app or site. Moreover, it is to be clarified that the data is not deleted with the “Clear History” button, rather your profile is disassociated with it removing any link that could be used to identify that it is yours.
Regardless, the recent announcement will indeed help Facebook move towards the good books of its security-conscious users and earn their trust, particularly since the Cambridge Analytica scandal.
Currently, this feature has been rolled out in a handful of countries only: Ireland, South Korea, and Spain. It will be available in other countries in the coming months as Facebook wants to make the transition slowly in order to ensure that it is working reliably once active.

Comments
Post a Comment