Last week, Capital One breach shocked the IT security community after it was revealed that a wannabe hacker was able to steal and brag about personal and financial details of over 106 million users. The incident also highlighted the fact that penetration testing has become more critical than ever.
If you’ve had the chance to lately go through an ethical hacking course, it is likely that you’ve come across the following 5 steps as an outline of the entire penetration testing process:
- Reconnaissance – Collecting maximum information about the target to make one’s attack process easier,
- Scanning – Identifying open ports, the services running on the host and any other vulnerabilities that can be detected,
- Gaining Access – Actually doing the attack using different techniques which may range from social engineering to purely technical exploits,
- Maintaining Access – Making sure that you have a backdoor that allows you continued access and does not alert the target,
- Covering Tracks – No one wants the FBI on their door, not even the great Kevin Mitnick.
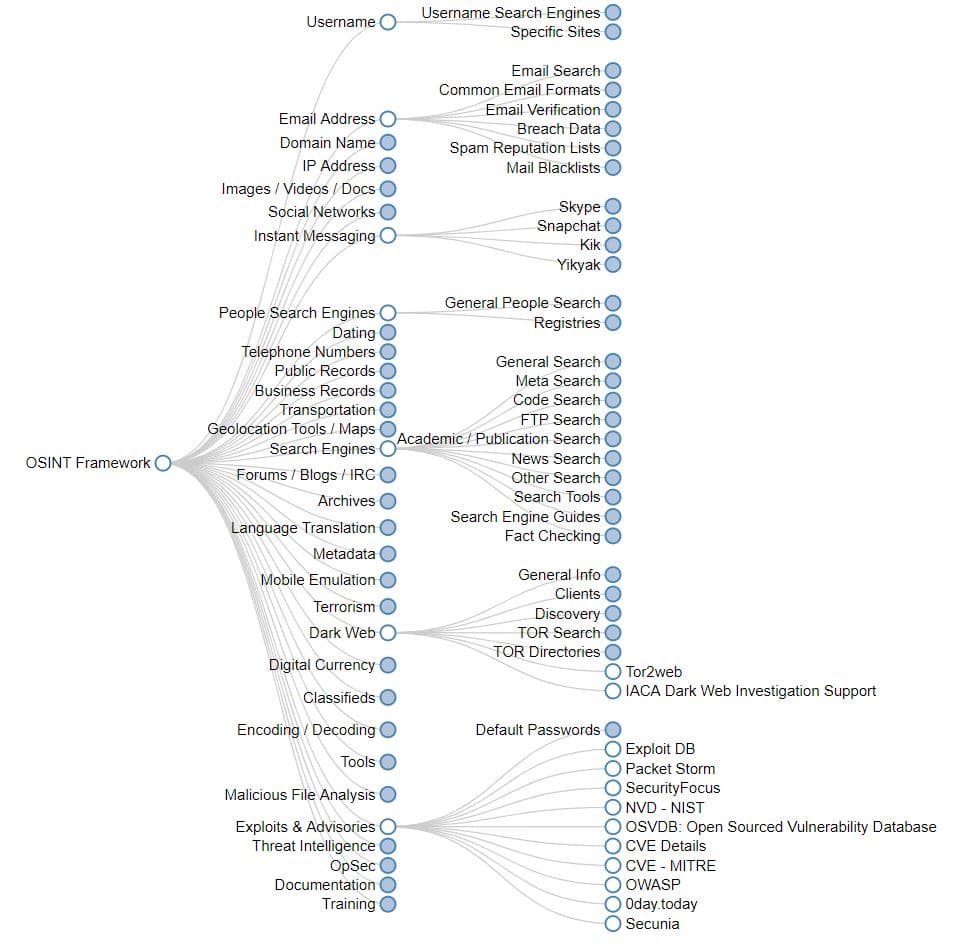
While all stages are of the utmost importance, the first one is where things actually get started. A common name given within the industry to data collected through it is called Open Source Intelligence (OSINT).
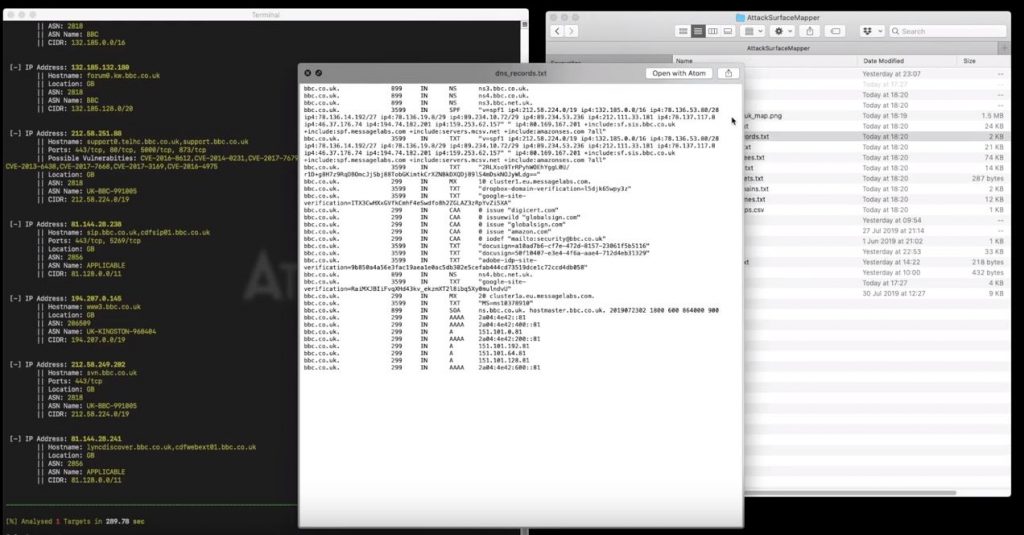
Recently at Blackhat, the cyber security firm Trustwave announced a new penetration testing tool called AttackSurfaceMapper (ASM) which has been developed in Python 3.x, is compatible with all major operating systems and helps one in doing just that.
The best part is that it saves the most valuable commodity that human beings can ever possess – time – making it highly efficient. How it does this is through a 3 step simplified process:
- The user enters the target domains, subdomains or IP addresses
- The tool uses the target identifier given in the previous stage to collect valuable intel available from a wide variety of public sources
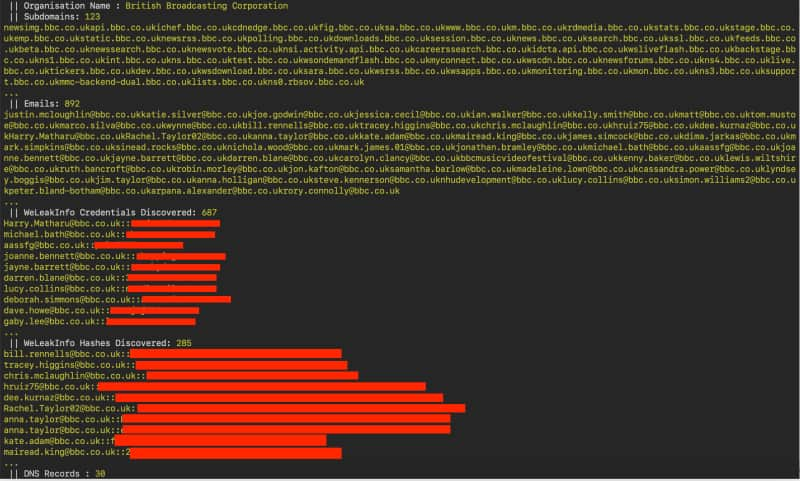
- The collected data which may comprise of emails, linked IP addresses, usernames, breached passwords, phone numbers, social media presences and much more is displayed with the user having the option to export it in HTML, CSV and TXT files.
In the words of the developers themselves on their official Github page where it can also be downloaded, the entire process after step 1, is as follows:
“Once the target list is fully expanded it performs passive reconnaissance on them, taking screenshots of websites, generating visual maps, looking up credentials in public breaches, passive port scanning with Shodan and scraping employees from LinkedIn. What this means is you’re left with hard actionable data gathered from these processes, targets to scan, websites to attack, email addresses to phish and credentials to brute force and spray,” wrote Trustwave in their blog post.
To conclude, AttackSurfaceMapper is one more tool which counts as a testimony to the huge advancements we’ve seen in the cybersecurity world over the past few years. The only drawback tools like AttackSurfaceMapper have is that while white-hat hackers can definitely use them to enhance the defenses of their systems, at the same time black-hat hackers can also make use of such publicly available tools for malicious purposes.
For the meanwhile though, the IT security community should make use of its capabilities to test their own assets since the benefit to be gained from it is immense.

Comments
Post a Comment