The malware attack involves two stages including one in which existing cryptomining malware is removed.
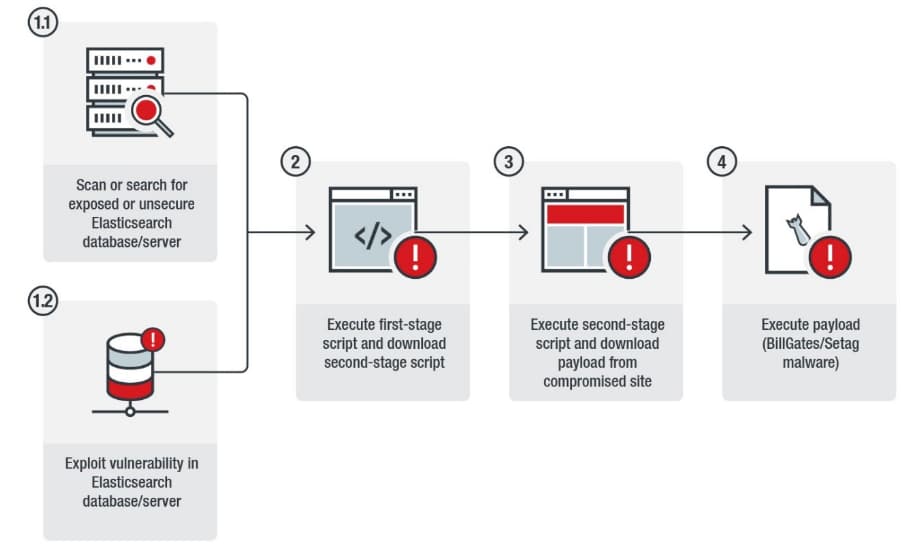
The IT security researchers at Trend Micro have discovered a new malware campaign targeting Elasticsearch databases in the wild.The campaign takes advantage of unprotected or publicly available Elasticsearch databases, infect them with malware before turning them into botnet zombies to carry out distributed-denial-of-service (DDoS) attacks.
According to researchers, the malware used in the attack is Setag backdoor originally discovered in 2017. Setag is equipped with capabilities like launching DDoS attacks and stealing system information.
Further analysis into the binaries unveiled presence of BillGates malware as well. BillGates malware surfaced back in 2014 bearing the same capabilities as Setag including launching DDoS attacks and compromising the targeted device.
The malware attacks in two stages. In the first stage of the attack, the malware runs script s67.sh to shut down the firewall and define which shell should be used. In the second stage of the attack, the malware deletes some files including various configuration files from the /tmp directory and existing cryprominers installed by other threat actors – All this to run its own operation.
“The ways that the scripts are retrieved are notable,” researchers said in their blog post. “Using expendable domains, for instance, allows the attackers to swap URLs as soon as they are detected.”
It is worth noting that threat actors are using compromised websites to drop their payload. Trend Micro researchers fear that abusing compromised websites may also let them evade detection of websites especially those developed by the attackers. These capabilities of the malware are a “red flag.”
“The cybercriminals or threat actors behind this attack used URL encoding, staged where the scripts are retrieved, and compromised legitimate websites could mean they are just testing their hacking tools or readying their infrastructure before mounting actual attacks.”Remember, ElasticSearch servers have a history with malware. In September 2017, Bob Diachenko, a security researcher identified over 4,000 ElasticSearch servers hosting PoS malware. In total Bob identified over 15,000 servers on ElasticSearch that did not possess any authentication and password protection.
Any business using Elasticsearch should watch out for the new attack. Elasticsearch has already issued a patch to fix the vulnerability exploited by this attack, therefore, implement the patch and secure yourself from becoming the next victim.

Comments
Post a Comment