MegaCortex ransomware was discovered in May this year.
iNSYNQ, a United States-based Cloud hosting provider has been hit by a massive ransomware attack crippling its cyberinfrastructure preventing customers from accessing their accounting data. It must be noted that iNSYNQ provides cloud-based QuickBooks accounting software and services.
The ransomware attack, according to iNSYNQ, took place on July 16th but the company released limited information which is being criticized by customers and IT security community. Though, since the company’s files were locked by ransomware understandably, restoring trove of data takes time.
It was only on July 19th at 4:40 p.m. ET when iNSYNQ updated its customers with a status on its support website stating that “iNSYNQ experienced a ransomware attack on 7/16/19 perpetrated by unknown malicious attackers. The attack impacted data belonging to certain iNSYNQ clients, rendering such data inaccessible.”
“As soon as iNSYNQ discovered the attack, iNSYNQ took steps to contain it. This included turning off some servers in the iNSYNQ environment. This effort was made to protect our clients’ data and backups,” the company said.
However, in another update earlier today, iNSYNQ’s CEO Elliot Luchansky wrote that their IT networks have been hit by MegaCortex ransomware, a new type of ransomware which surfaced online in May this year.
“While we caught the attack early, the malware was able to encrypt some files,” Luchansky said. “We are currently working to determine if those are recoverable.”“You might see encrypted files on your desktop with .megacortex as an extension,” Luchansky added. “They aren’t available to access.”“Luckily, the vast majority of the files that were impacted (i.e., are encrypted) are smaller files and do not include QuickBooks or Sage files,” he added.
Vitali Kremez, an IT security researcher has tweeted an in-depth analysis of MegaCortex ransomware revealing that its prime target is online businesses.
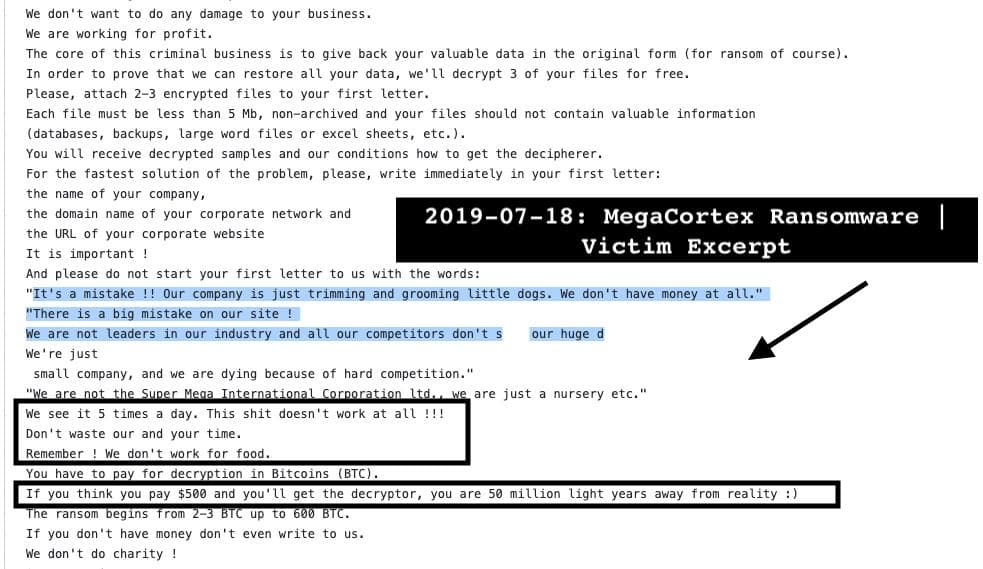
A screenshot of MegaCortex ransomware’s note shows that cyber criminals behind this campaign are here to make big bucks as their ransom demand starts from 2-3 BTC and goes up to 600 BTC and if the victim does not have this amount they should not bother to reply to the note.
“And please do not start your first letter to us with the words: It’s a mistake !! Our company is just trimming and grooming little dogs. We don’t have money at all. There is a big mistake on our site,!” says the ransom note.
A full preview of the ransom note is available below:
In iNSYNQ’s case, Luchansky did not reveal exactly how much ransom was demanded by the attackers. The good news, however, is that according to a recent update, iNSYNQ is in the process of restoring customers’ accounts but it may take a few days.
Meanwhile, Luchansky suggests that those customers who are still having their files locked should use old backups or contact the company in case they require assistance. Here is the full statement from the company’s CEO:
“While I cannot share details on the specific ransomware or the number of servers affected, I can share that iNSYNQ and our customers are the victims of a malware attack that’s a totally new variant and hadn’t been detected before, confirmed by the experienced and knowledgeable cybersecurity team we’ve employed.”
“Unfortunately, we have to keep the detail fairly minimal, as I’m sure you’re familiar with in these sorts of situations. Our customers and their data is our number one priority. Transparency is something we pride ourselves on, and it’s difficult to hold back. However, the lack of detailed information in this situation is purposeful. We’re in behind the scenes trench warfare doing everything we possibly can to secure and restore our systems and customer data and backups, and too much information around this situation puts us and our customers at risk.”
“My team will continue to work around the clock to secure and restore access to all impacted data, and we believe we have an end in sight in the near future.”
Ransomware attacks are bad for business. In fact, according to the Internet Society’s Online Trust Alliance (OTA),ransomware-type attacks caused $8 billion damages last year. These attacks consisted of stealing data from a user via malware before demanding ransom in return for unlocking the data – It is believed that ransomware attacks will grow to cost $20 billion in 2021.
Therefore, keep a backup of your data at all cost and use a reliable anti-virus. Also, here is a guide for users on how to prevent the growing issue of encryption-based malware (Ransomware).

Comments
Post a Comment